Reentrancy
A reentrancy attack is a highly-damaging exploit commonly found in Solidity smart contracts. This type of attack occurs when a function within a contract makes an external call to another contract whose trustworthiness cannot be guaranteed. Subsequently, the untrusted contract can make a repeated call back to the original function, often with malicious intent to siphon off funds.
In instances where the contract neglects to update its state before transferring funds, the attacker can repeatedly invoke the withdraw function to deplete the contract's funds. One of the most notorious real-world examples of a reentrancy attack is the DAO attack, which resulted in the loss of $60 million USD.
Vulnerability in simple terms
#
Let's say that contract A calls contract B. The reentrancy exploit allows B to call back into A before A finishes execution.
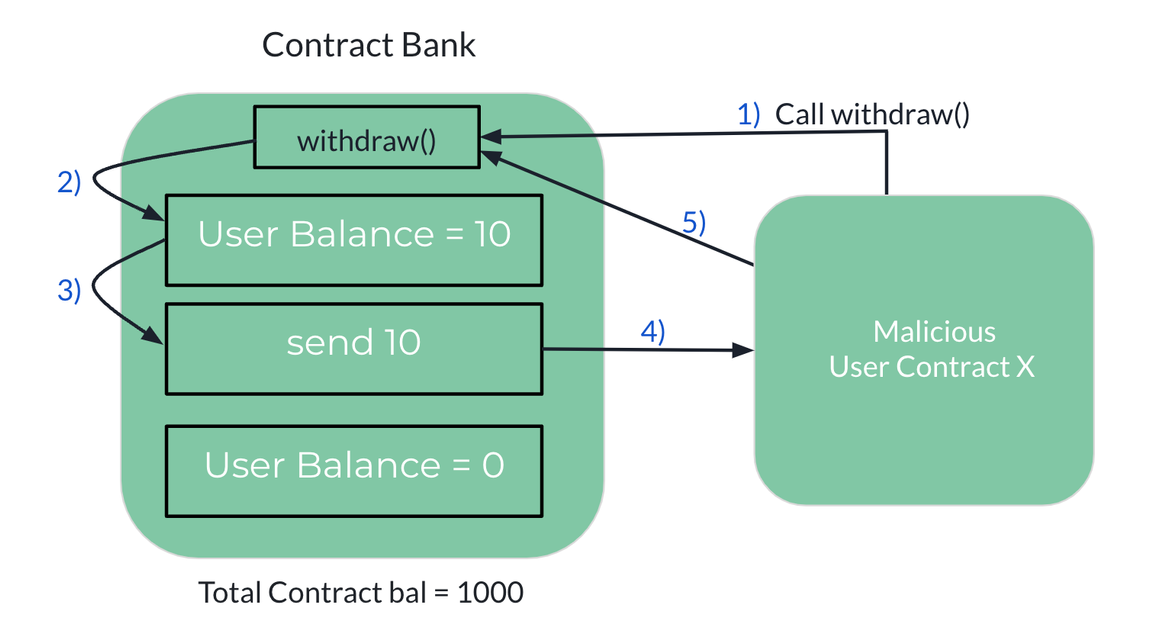
Step by step explanation:
Assume contract X has a balance of 10 ETH in the contract bank (bank contract has total 1000 ETH locked in it which contributes to funds of all user balances)
- Contract X initiates transaction to withdraw all its Funds from contract Bank
withdraw()checks balance of user X=10 ETH- Transaction is being initiated to send 10ETH to user X
- 10 ETH has been sent to User X
- Contract X on receiving funds, initiates a new
withdraw()transaction to contract bank. - Since the balance has not been yet set to 0, the user can again withdraw 10 ETH
- Thus, the Contract X recursively reenters and withdraw funds until the contract bank is drained.
Technical Contract Flow
#
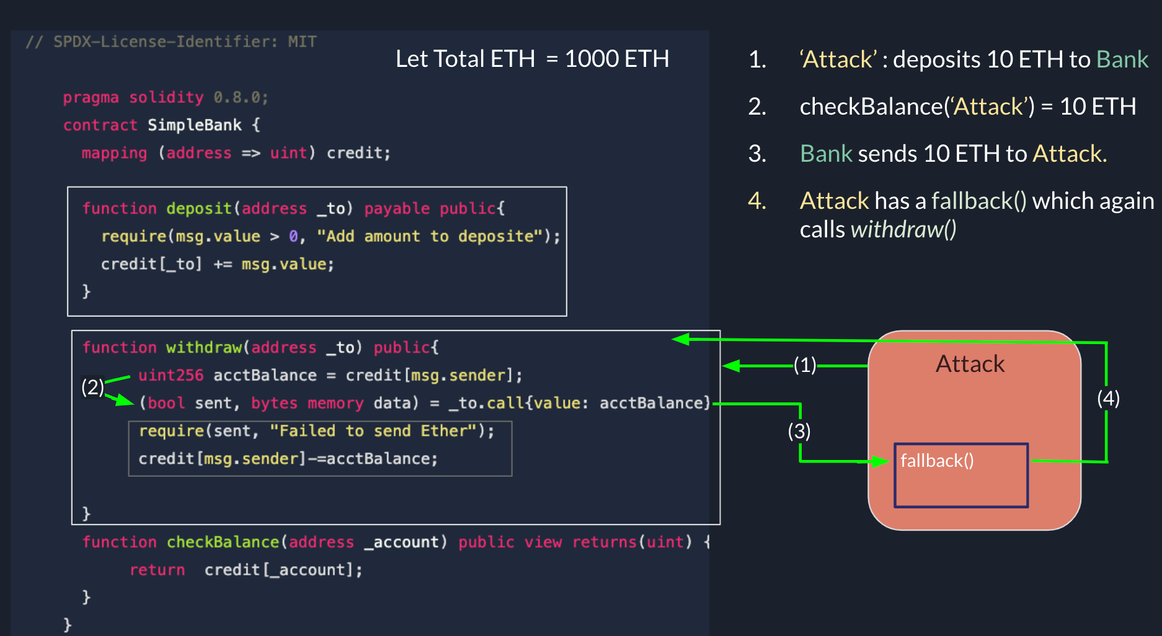
The same attack explained above is shown in context with a Contract and its work of flow on reentrancy attack.
Hidden Balance Update
