Hidden Mint
Detects Suspicious and Malicious minting of tokens.
Flags Tokens in which the additional minting / supply of the token can be altered in a malicious way.
Context and some definitions:
#
- Minting refers to creating new tokens and adding them to the circulating supply. When there are more tokens, assuming the demand stays constant, the increase in supply could lead to a decrease in the token's price.
- Nevertheless, when the mint functions are prone to an ill-intentioned call, it takes to destroy a token's value.
What’s wrong when The owner can mint an unlimited supply...?
#
- Although this practice is commonly seen in token contracts, it introduces an attack vector that could result in wiping the token's value.
- In this scenario, one actor could maliciously mint an unlimited amount of tokens to his wallet, sell them, or use them for market manipulation and as a result, massively decrease the token's price
- For example, In 2021, Levyathan.finance suffered an attack where a malicious actor accessed a wallet's private keys on GitHub. The wallet had unlimited minting permissions, enabling the attacker to mint and dump 100,000,000,000,000,000,000,000,000 LEV tokens which led to a price drop to nearly 0, causing a $1.5 million loss
Subcategories marked by API
#
Hidden Internal Mint
- Finds functions which exploits your gas fees to mint additional tokens than asked for.
- Lets say you want to mint 1000 Tokens, but the transaction maliciously uses your gas fees to mint some additional tokens to other (say administrator) addresses.
Controlled Mint
- Detects controlled functions, through which administrators can mint an infinite number of tokens, thus making it easy controlled liquidity option
Upd Supply
- Detects functions which can manipulate the
totalSupplyof the token - These functions can be used to present a fake value of the current total supply, thus giving people a fake sense of acceptance of the token.
Sample Malicious Token Contract
#
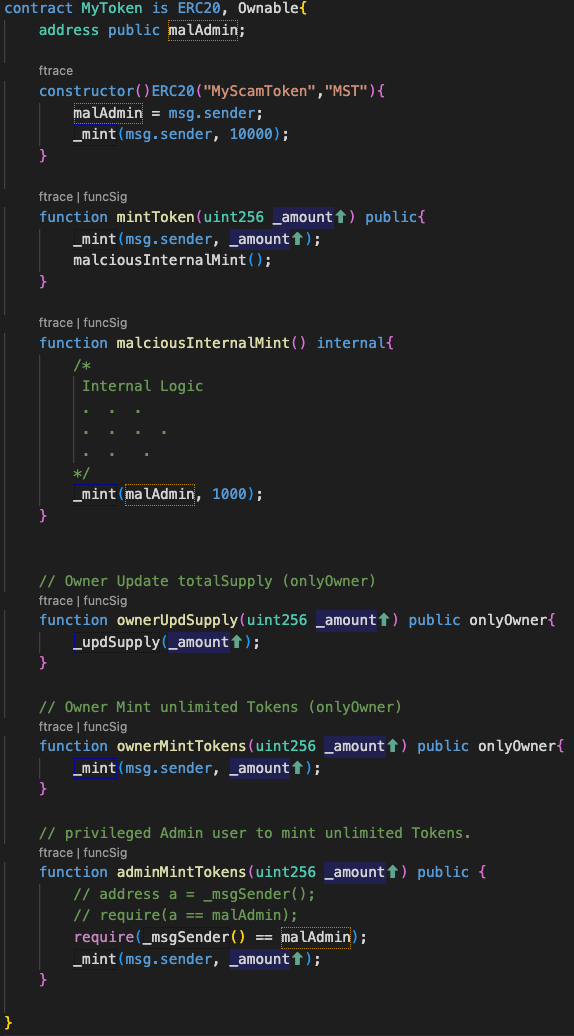
List of functions in the contract:
mintToken() , malciousInternalMint() , ownerUpdSupply() , ownerMintTokens() , adminMintTokens()
Malicious functions to look out for:
mintToken():- Typically this function is meant for users to mint tokens as per the contract requirement.
- Internally, the function triggers the
malciousInternalMint()- this hidden function exploits user’s gas fee and mints additional tokens to a malicious address.
- This function is flagged for
hidden_internal_mint
ownerUpdSupply():totalSupplyof a token is the total current supply of the token available in the market.- Total supply is part of a cryptocurrency project's tokenomics and influences its value proposition, pricing dynamics, market capitalization, and even its utility. The total supply can be capped or uncapped.
ownerUpdSupply()alters thetotalSupplyof the token as directed by the contract (which is not acceptable).totalSupplyshould be only increased on minting and decreased only on burning, any other alteration is STRICTLY BAD BEHAVIOR. If discovered, this function will be flagged forupd_supply.
-ownerMintTokens() & adminMintTokens() :
- These functions from a logical perspective mint the mentioned amount of tokens to the given address.
- What is concerning is that they are accessible only to certain address.
- These addresses can mint infinite number of tokens as and when required.
- The above contract mentioned is a basic token contract. Now imagine a case where the contract is pausable, then these malicious actors can use these controlled functions to mint tokens, while pausing the other minting functions. This makes way for instant controlled liquidity and and easy exit strategy for the contract owner.
- These functions are thus flagged for
controlled_mint
Other features to look out for:
#
- One good informational feature to know about the token is the contract pre-mints some amount of tokens (these may be developer / whitelist address) at the time of deployment.
- Thus we have the constructor in place as a flag for
pre_mint
API Output:
#
Previous
Threats and Labels
