Hidden Balance Update (High Risk)
Suspicious and/or malicious balance updations.
What Balance?
#
- Lets say a user A (0x123…456) holds token (ie. USDC)
- if he holds 1000 USDC, it means user A’s balance of USDC is 1000
balanceOf(0x123...456) = 1000
Malicious Balance Updation
#
- Balance is usually updated during the invocation of
mintburn, andtransfer - Any other updation of the user's balance is directly not encouraged, and will be considered malicious
- This is similar to tampering with your bank balance without your direct intervention
Sample Malicious Token Contract
#
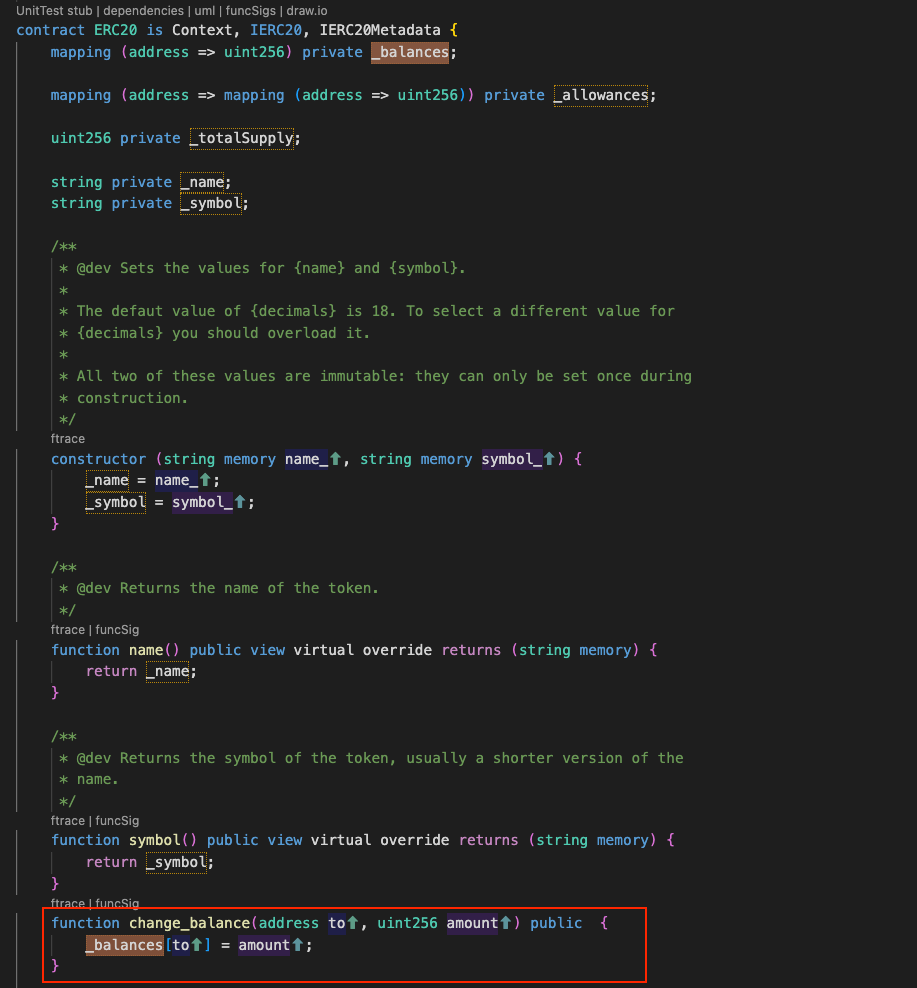
Above is a basic ERC20 contract, with a additional function change_balance() .
The function change_balance() although looks simple has direct access to write/update balances which is dangerous for the security of the contract.
Exploit Case
#
Suppose let the above be the token contract of say Token ABC.
- Lets say user A (0x123…456) holds 1000 ABC tokens
- Now anyone can call
change_balance()to update userA’s balance.change_balance(0x123...456 , 100)will update userA’s balance to 100
API Output
#
Conclusion
#
The API identifies and flags contracts and respective functions contributing towards malicious and inappropriate updation of token balances.
Previous
Hidden Mint
Next
Reentrancy
