Malicious Bool Checks
This facet flags functions which does pause-like functionality checks, and can potentially block transfer, approval or allowance of tokens.
Context
#
Base ERC functions like transfer() , allowance() and approval() should be accessible to end-users. Malicious contracts may block the execution of these base functionalities by doing certain bool checks, making these functions usable to users only when certain variables/functions are set to true .
Scenarios
#
Pause like checks
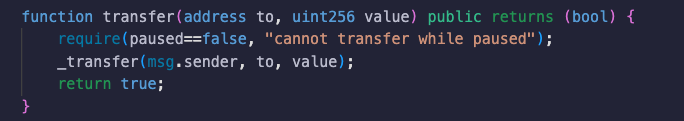
Here, for a transfer to execute, there is a direct condition check of whether paused is set to false .
These are straightforward checks which block the execution of base ERC functionalities.
Backdoor-Pause like checks
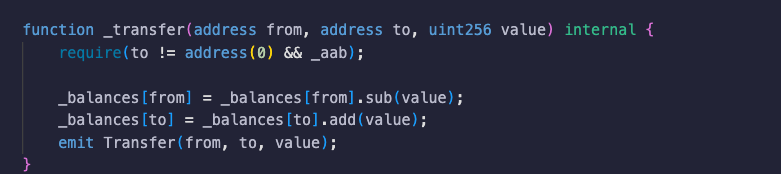
Here, for a transfer to execute, the variable _aab needs to be set to true .
This leads to backdoor-like pause functionalities, where the variable acts as a pausing check, which deceptively blocks the execution of token transfers.
Checkpoint article reference
#
Contract address : https://bscscan.com/address/0x31d9bb2d2e971f0f2832b32f942828e1f5d82bf9#code
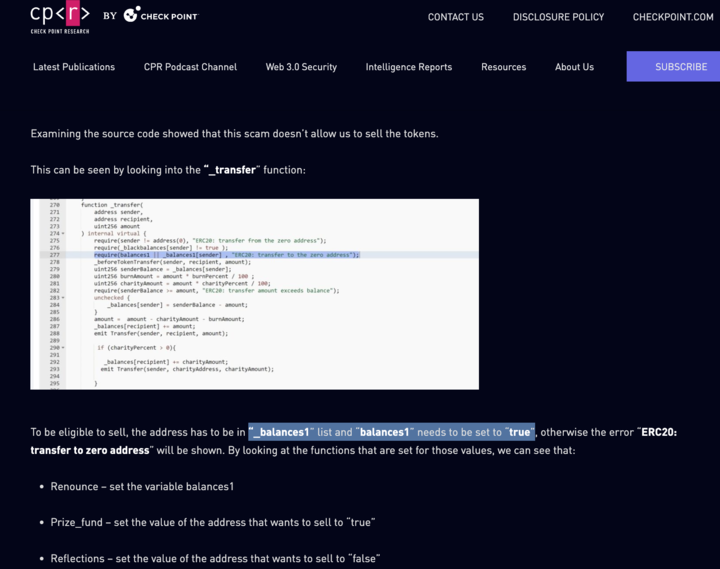
Here, the contract 0x31d9bb2d2e971f0f2832b32f942828e1f5d82bf9 , has function _transfer()
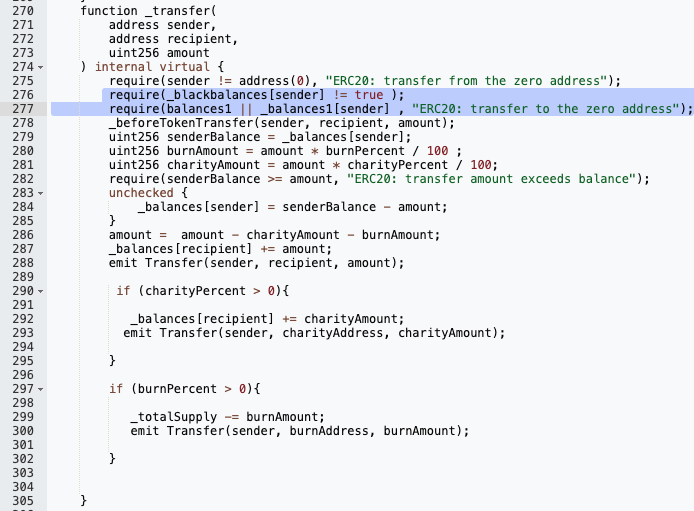
Here, line 267 and 277 are classic examples of above cases where:
Line 276: Potentially blocks certain users from transferring tokens (blacklisting users)
Line 277:
The variable balances1 needs to be set to true , for transfer to happen. otherwise it will result in the error “ERC20: transfer to zero address”
Facet API results:
#
Facet API results on the contract mentioned in checkpoint article above 0x31d9bb2d2e971f0f2832b32f942828e1f5d82bf9
As mentioned in the above article, our module flags all the transfer() functions which involves the assertions of balances1 and _balances1 , along with the assertion statements. Adding to the article, it also give statements which restricts certain users from transferring tokens (blacklisting users).
Unchecked Low Level Calls
Malicious Burn
